System Center Endpoint Protection For Mac
Related services: Endpoint Protection, Certified Desktop, CrowdStrike Endpoint Protection
Microsoft announced in November 2018 that it was discontinuing support for System Center Endpoint protection for Mac on December 31, 2018. As a result, OIT is transitioning to ESET Endpoint Antivirus as the recommended antivirus software for university owned Mac computers. See the ESET Endpoint Antivirus page fto learn how to download and install the antivirus agent.
- For Windows 7 systems, the Endpoint Protection Downloads page offers a link to Microsoft Security Essentials, though it is important to note that Windows 7 is End of Life as of January 14, 2020. Johns Hopkins faculty, staff, and students may use Microsoft Defender at no cost on computers owned by the University or Health System as long as they.
- Endpoint Protection Client for Mac Computers and Linux Servers. System Center includes an Endpoint Protection client for Linux and for Mac computers. These clients are not supplied with Configuration Manager; instead, you must download the following products from the Microsoft Volume Licensing Service Center.
- Advanced Systems International. USB Control & Lockdown Software to Block USB.
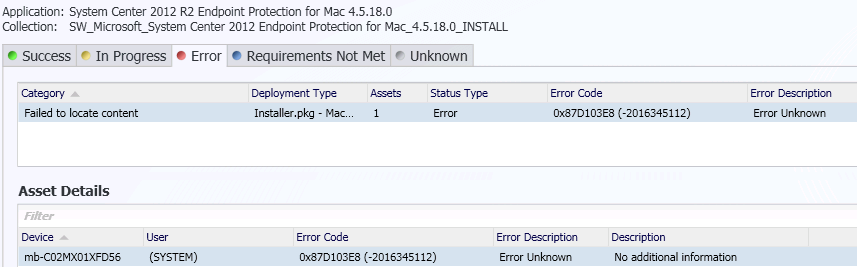
Microsoft will end support for all Mac versions of System Center Endpoint Protection (SCEP) on Monday, December 31, 2018. If you're currently using any version of SCEP for Mac, plan to migrate to a replacement endpoint protection product for Mac clients.

Cornell policy requires all university-owned computers to use antivirus protection, and strongly recommends the same for any computer used by a member of the Cornell community. Local IT support administrators who have onboarded with Certified Desktop can deploy CrowdStrike for Mac, providing antivirus scanning and endpoint malware protection and response. Learn more about antivirus options for Mac.

If you have any questions, contact your local technical support provider or email anti-virus@cornell.edu.
I thought I was done with SCEP (see parts 1, 2 and 3) but whilst undertaking an exercise looking into using SCEP on some Linux servers (and specifically looking at how it can provide reporting data to SCOM via a Management Pack), I inadvertently came across a little-documented command line argument for one of its binaries, scep_daemon.
The documentation for the Linux SCEP SCOM Management Pack (what a mouthful!) vaguely alluded to feeding data to SCOM via a –status argument. This argument isn’t mentioned anywhere else in SCEP’s Linux documentation, nor listed when you invoke scep_daemon –help on either platform.
The Linux version of SCEP is also a rebranded version of ESET, just like its macOS counterpart and the above scep_daemon binary is also present in that version, so I thought I’d experiment in macOS…
There is a brief mention in the macOS documentation on the installer ISO, but the path to the binary is wrong (it says /Applications/.scep/scep_daemon). The scep_daemon binary is actually here:
But we’ll refer to it as scep_daemon from now on (just to keep my examples shorter and sweeter).
System Center Endpoint Protection Microsoft
Running the macOS scep_daemon binary with the –status argument surprisingly yields the following:
The results pretty much speak for themselves in terms of what they mean and you can easily scrape them to get individual snippets.
For example, to get the status of the Real Time Protection (on access) scanning engine:
This will return “Enabled” or “Disabled”. You could easily spin this into an Extension Attribute for Jamf Pro, for example:
| #!/bin/bash |
| status=$(/Applications/System Center Endpoint Protection.app/Contents/MacOS/scep_daemon –status | grep RTPStatus | cut -d '=' -f 2) |
| echo'<result>$status</result>' |
| exit 0 |
You could report on it with an Advanced Search or even use it as the criteria for a Smart Group, creating a remediation policy that runs a script to re-enable protection if it’s disabled. We just need a little help from our old friend, scep_set, for example (see part 1 for a more thorough overview of using it):
| #!/bin/bash |
| /Applications/System Center Endpoint Protection.app/Contents/MacOS/scep_set –section fac –set='action_av = 'scan'' |
| sleep 1 |
| launchctl unload /Library/LaunchDaemons/com.microsoft.scep_daemon.plist |
| sleep 1 |
| launchctl load /Library/LaunchDaemons/com.microsoft.scep_daemon.plist |
| exit 0 |
Install System Center Endpoint Protection

As a bonus, if you’ve ever ran scheduled or ad-hoc on demand scans, scep_daemon –status will report extra results including the type of scans run (Quick Scan and Deep Scan), the directory path they were targeted to, when they were last run and if they were interrupted, for example:
